What are proxy chains?
Proxychains is a tool that forces any TCP connection made by any given operation to go through delegates like Escarpment or any other SOCKS4, SOCKS5 or HTTP delegates. It’s an open-source design for GNU/ Linux systems. Basically, you can use ProxyChains to run any program through a deputy garçon. This will allow you to pierce the Internet from behind a restrictive firewall, hide your IP address, run operations like SSH/ telnet/ wget/ FTP and Nmap through deputy waiters, and indeed pierce your original Intranet from outdoors through an external deputy. Proxychains indeed allow you to use multiple delegates at formerly by “ chaining ” the delegates together and to use programs with no erected-in deputy support through a deputy.
Installation on Kali Linux
Step 1.
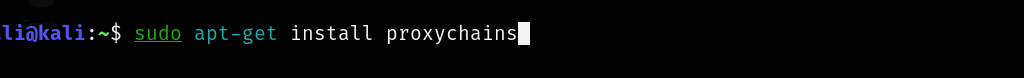
Step 2.
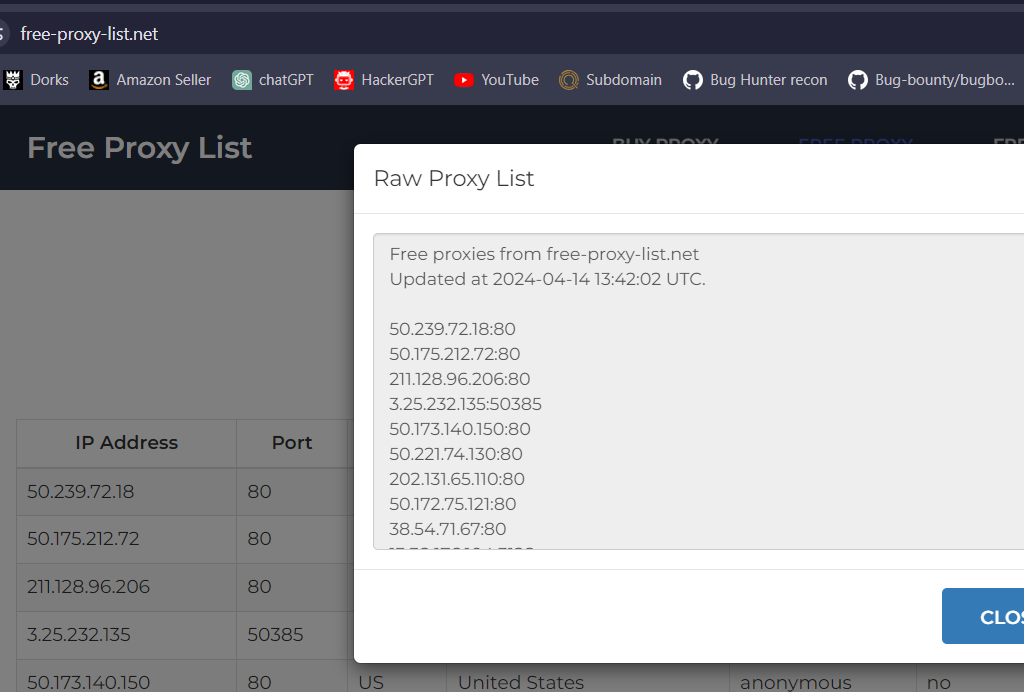
Step 3. Go to Google and search for free proxy lists
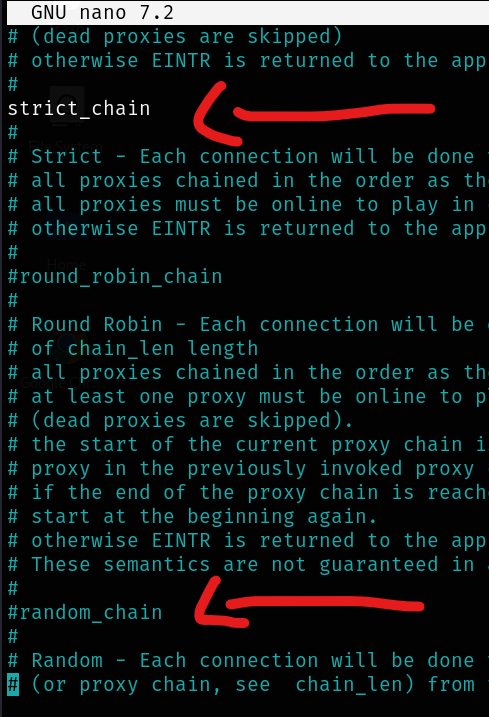
Step 4. Uncomment the lines from below image
Step 5. Go to last lines and paste the proxies that you copied
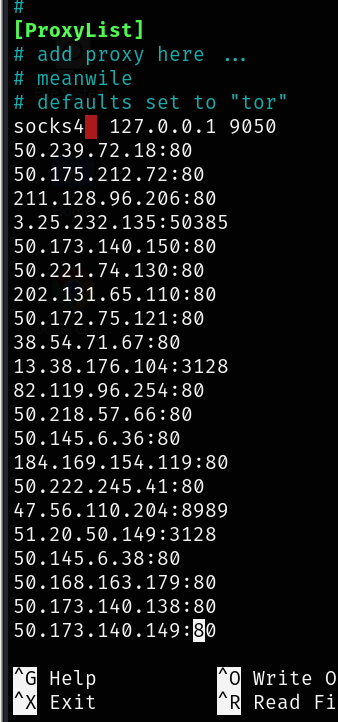
Now you are all set.
Now just type: `proxychains firefox` browser will open with built-in proxies and now you are Anonymous